5. National Cybersecurity Strategy Good Practice
ISBN (Electronic Publication) 978-92-61-42091-8
5. National Cybersecurity Strategy Good Practice
Cybersecurity affects many areas of socio-economic development and is influenced by several factors within the national context. Therefore, this section introduces a set of good-practice elements that can make the Strategy comprehensive and effective, while allowing for tailoring to the national context.
These good-practice elements are grouped into distinct focus areas, overarching themes for a comprehensive NCS. While both the focus areas and the good-practice elements have been put forward here as examples of good practice, it is particularly important that the latter are viewed in the national context, as some may not be relevant to a country’s specific situation. Countries should identify and follow the good-practice elements that support their own objectives and priorities in line with the vision defined in their Strategy (Section 4.1). The order of the individual elements or focus areas below should not be seen as indicating a level of importance or priority.
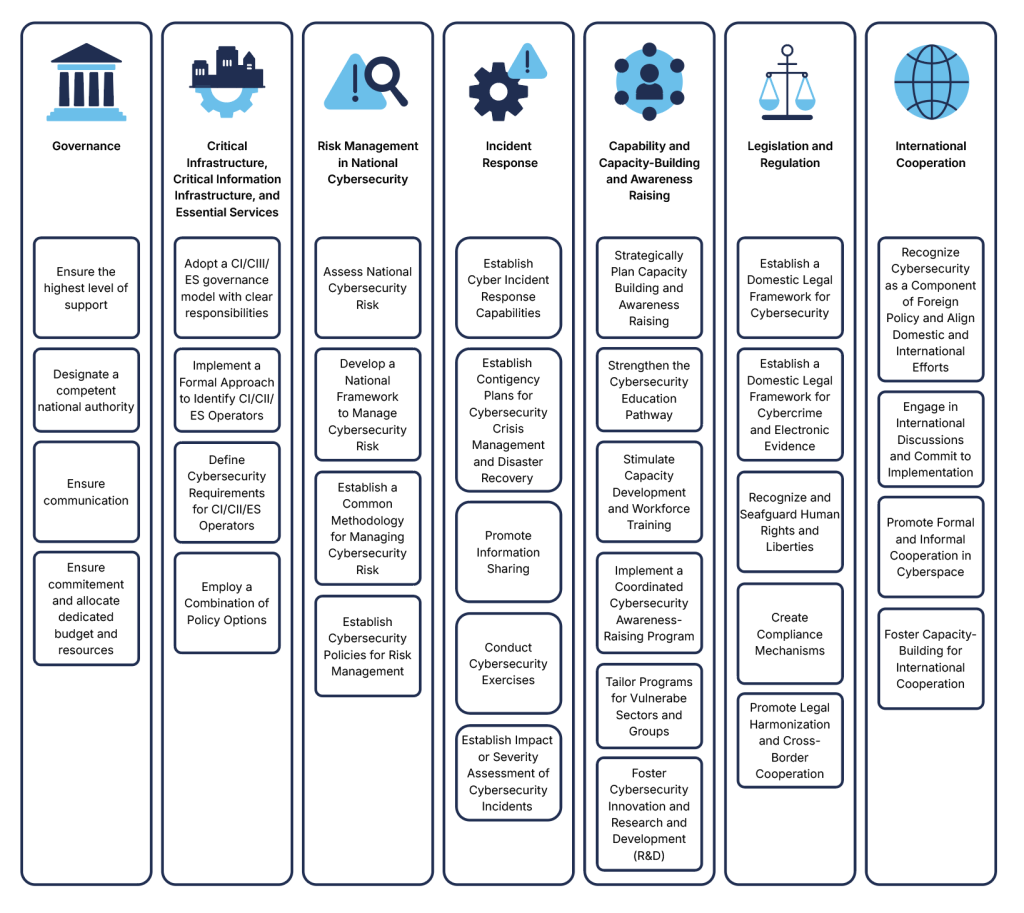
5.1 Focus Area 1 – Governance
This focus area introduces good-practice elements for governance structures, models, and frameworks for national cybersecurity that can be included in the Strategy. This includes clearly stating the strategic objectives and outcomes the government intends to pursue at the political, operational, and technical levels to increase national resilience and reduce risks to people, companies, critical infrastructures, services, and assets. The Strategy should also identify the roles, responsibilities, authority, powers, and accountability mechanisms of the stakeholders tasked with implementing the Strategy, such as the competent national authority (where applicable).
5.1.1 Ensure the highest level of support
The Strategy should have the formal endorsement of the highest level of government. This endorsement serves two important purposes. First, it improves the likelihood that sufficient resources will be allocated and that coordination efforts will be successful. Second, it signals to the broader national ecosystem that the country’s cybersecurity is intertwined with its digital economy and other social and political aspects that depend on digital systems, and therefore must be treated as a national priority.
The Strategy may also need to be codified in the domestic legal framework to obtain national relevance and prioritization.
5.1.2 Designate a competent national authority
Effective national cybersecurity governance requires the designation of one or more competent national cybersecurity authorities, depending on the country’s size and constitutional structure. In federal or decentralized systems, multiple authorities may be necessary. These authorities should be explicitly identified in the Strategy as responsible for leading and coordinating cybersecurity governance, providing guidance and support for its implementation. To ensure authority and effectiveness, they should be anchored in, or closely connected to, the highest level of government or national leadership, enabling them to provide strategic direction, coordinate action, and monitor implementation.
Tasks of the competent authority may include preparing draft laws and policies on cybersecurity governance, defining and clarifying roles, responsibilities, processes, and decision rights, and ensuring effective implementation of the Strategy. Given that cybersecurity is a cross-cutting domain, it is important that the competent national authority can involve and direct relevant stakeholders. This includes identifying and overseeing the stakeholders responsible for operational tasks or initiatives and establishing related performance targets.
The competent authority should also be responsible for reporting on the progress and outcomes of cybersecurity activities. To facilitate reporting, responsible stakeholders and government entities should be mandated to report back to the competent national authority in measurable terms. Using key performance indicators (KPIs) is an effective way to assess progress and promote accountability by enabling oversight (see Section 3.6 for a description of SMART KPIs).
To enable the competent authority to carry out its tasks, it should be given a clear mandate over all relevant stakeholders. This mandate may have to be formalized in policy or law to empower the authority to perform its functions.
5.1.3 Ensure communication, coordination, and collaboration
Cybersecurity requires a whole-of-nation approach, drawing on the efforts of all of society, and must be built on successful cooperation between different stakeholders, including public and private actors. A national cybersecurity governance system should define the roles, responsibilities, processes, and relationships among various stakeholders to ensure effective, efficient, and accountable delivery of cybersecurity.
The allocation of roles and responsibilities should align with each stakeholder’s mandate within the country’s constitutional and legal framework. For example, government bodies may deliver public services, civil society may provide oversight and advisory support, and the legislature may be responsible for lawmaking.
Governance must therefore address actors across multiple dimensions, such aslaw and policy, strategy, operations, and technology, and operate across organizational, local, national, regional, and international levels.
5.1.3.1 Ensure intra-government cooperation
The Strategy should identify and include the government entities affected by or responsible for its implementation. Intra-governmental commitment, coordination, and cooperation are core functions of governmental institutions and are essential to ensure that governance mechanisms (e.g., standards, regulations, market incentives) and resources yield the desired outcomes of the Strategy. Having a well-established and high-level national cybersecurity competent authority will also help enhance intra-government coordination and cooperation.
Effective communication, coordination, and collaboration ensure that all ministries and government agencies are aware of each other’s respective powers, missions, and tasks. Examples include periodic meetings involving relevant stakeholders and the creation of an intra-government task force to address a particular issue.
Intra-government coordination mechanisms should also ensure that cybersecurity policies and actions are consistent across ministries and government agencies, avoiding duplication and promoting coherence with the country’s broader digital transformation agenda.
5.1.3.2 Ensure sectoral cooperation
The national cybersecurity governance structure should reflect an understanding of the dependencies that the government has on the private sector and other non-governmental stakeholders (and vice-versa) so they can work together on achieving a more secure, safe, and resilient ecosystem in line with the principle of inclusiveness (Section 4.3). To this end, the Strategy should articulate how the government will engage these non-governmental stakeholders and clearly define their roles and responsibilities within the governance framework.
It is good practice for the Strategy to call for the identification of a network of authoritative national contact points for industries essential to the operation and recovery of critical services and infrastructures. Roles assigned to each stakeholder should be consistent with their overall mandate within the national legal and institutional framework.
The Strategy should also be aligned with other national priorities, such as ensuring connectivity is affordable, available, and inclusive; advancing data protection and privacy while promoting innovation; strengthening infrastructure resilience and service availability in the face of disasters, climate change, and pandemics; responsibly exploring and adopting emerging technologies such as AI, blockchain, quantum computing, and distributed ledger technologies. Such alignment ensures that sectoral cooperation on cybersecurity is not siloed, but embedded in broader national objectives for digital transformation, resilience, and sustainable development.
5.1.4 Ensure commitment and allocate dedicated budget and resources
Successful national cybersecurity efforts require political commitment and leadership, underpinned by trusted partnerships. Commitment in this context means supporting consistent policies over time to ensure national cybersecurity priorities are delivered. A good practice is to establish safeguards ensuring consistency between the country’s domestic and foreign policy agendas, so one ministry does not undermine another by presenting conflicting positions on the same policy issue (e.g., trade flow vs. export control of dual-use technologies).
This long-term perspective should also apply to cybersecurity governance with respect to emerging technologies: while remaining technologically neutral, it should establish resilient mechanisms to anticipate and manage technological change as the landscape evolves.
Another critical element of national cybersecurity that requires commitment is resourcing. Sufficient, consistent, and continuous funding is foundational to an effective national cybersecurity posture. Governance structures must be designed with dedicated budgets that provide relevant stakeholders with the resources required to carry out their tasks. Resources should be defined in terms of money (i.e., dedicated budget), people, and materials.
The objectives and tasks within the Strategy should not be viewed as a one-time allocation of resources. Resource requirements should be revisited regularly based on progress or shortfalls in implementing tasks or objectives within the Strategy. The government may also consider establishing a central cybersecurity budget managed by a national governance mechanism. Whether consolidating disparate funding sources into a coherent, integrated program or creating a unified intra-governmental budget, the overall program should be managed and tracked through milestones to ensure successful implementation.
5.2 Focus Area 2 – Critical Infrastructure, Critical Information Infrastructure, and Essential Services
This focus area examines good practices for identifying and protecting Critical Infrastructure (CI), Critical Information Infrastructure (CII), and Essential Services (ES), as well as for strengthening their reliability and resilience.
The potential consequences of an incident impacting CI/CII/ES can be severe, disrupting social order, interrupting the delivery of services, and undermining the economic well-being of a country. The Strategy should therefore emphasize the importance of risk management and resilience efforts aimed at reducing the likelihood and impact of such disruptive or destructive incidents.
There are no universally recognized definitions for CI/CII/ES, which may ultimately depend on geopolitical, socio-economic, and cultural characteristics of the national context. Governments should therefore define these terms based on their national cybersecurity risk assessments, circumstances, and priorities.
This Guide recognizes the lack of common terminology and adopts a flexible approach that allows for different interpretations of the concepts of CI/CII/ES and related operators. These infrastructures and services are highly interdependent, with the functioning of one often relying on others, and disruptions in one area can cascade across multiple systems. Examples include:
- Critical Infrastructures (CI): assets essential to the functioning and security of society and the economy (e.g., power plants, water treatment facilities, rail networks).
- Critical Information Infrastructures (CII): ICT and operational technology systems (IT and OT) that support key functions of critical infrastructure (e.g., Internet Exchange Points (IXPs), submarine cables, Supervisory Control and Data Acquisition (SCADA) systems, and national data centers).
- Essential Services (ES): services necessary to sustain critical societal or economic activities (e.g., electricity supply, digital and mobile communications, public transportation, healthcare services).
- CI/CII/ES Operators: public or private entities that own or operate CI and/or CII and provide ES (e.g., Internet Service Providers (ISPs), Domain Name Service providers (DNSs), telecom operators, major hospitals, central banks, water and energy utilities, etc.)
- Service Level Agreements (SLA): formal contracts or agreements between CI/CII/ES operators that define expected service levels, performance metrics, responsibilities, and response mechanisms required to maintain operational continuity and resilience across interdependent systems.
5.2.1 Adopt a CI/CII/ES governance model with clear responsibilities
The Strategy should, at a high level, define the governance structure, roles, responsibilities, and coordination mechanisms of the various stakeholders involved in CI/CII protection, in accordance with the principle of clear leadership, roles, and resource allocation (Section 4.8).
Because CI/CII/ES protection often exceeds the capacity of any single government agency, appointing an overall coordinator for CI/CII/ES cybersecurity, such as an interagency committee, can significantly strengthen coordination and protection efforts.
The governance model for CI/CII/ES protection should include: the identification of government entities in charge of specific sectors; the responsibilities and accountability of operators; the establishment of communication channels and cooperation mechanisms between public and private actors to ensure the continuity and recovery of critical services; mechanisms to promote coordination and alignment among government entities with overlapping mandates; and ways to ensure that sectoral regulators create clear, consistent security requirements that avoid duplication, prevent waste of resources, and streamline compliance efforts across both public and private sectors.
Given the cross-border nature of CI/CII/ES, the governance model should also include mechanisms for regional and international coordination and collaboration.
5.2.2 Implement a Formal Approach to Identify CI/CII/ES
The Strategy should promote the identification of CI/CII/ES through a formal, repeatable, and criteria-based approach. This process should be centrally coordinated, periodically reviewed, and used to inform national risk management, resource allocation, and incident response planning. Outputs typically include a national register of critical sectors, services, functions, operators, and assets, with associated levels of criticality and risk profiles.
While a variety of methodologies exist to identify CI/CII/ES, countries might consider applying sectoral, functional, and impact criteria, such as dependencies and interdependencies with other infrastructure, relevance of the infrastructure for maintaining minimum service levels, redundancies, market share, and geographic location.
Reviews should occur at regular intervals (e.g., every two years) or after major incidents or technological changes to ensure the registry remains accurate and relevant. Early and continuous involvement of relevant stakeholders, including public authorities, regulators, and private infrastructure operators, is essential. The Strategy should also encourage or incentivize private operators to conduct regular Business Impact Analyses (BIAs) and Risk Assessments. These assessments should evaluate the potential effects of disruptions on critical assets, operations, and functions, and their outputs should be shared with relevant authorities to inform national-level identification, business continuity, and disaster recovery planning (Sections 3.2.2, 5.3.1, and 5.4.2).
The Strategy should establish feedback loops to integrate lessons learned from incidents, exercises, and audits into future identification cycles, and promote convergence with regional and international frameworks to support cross-border consistency.
5.2.3 Define Cybersecurity Requirements for CI/CII/ES Operators
The Strategy should either highlight the existing or promote the development of new legislative and regulatory frameworks outlining cybersecurity requirements for CI/CII/ES operators and other relevant stakeholders (in accordance with Section 5.6.1 on Legislation and Regulation). These requirements should be structured so that the targeted operators meet a minimum baseline of cybersecurity practices, while also maintaining flexibility to align with their own risk management priorities.
Baselines should leverage internationally recognized standards and good practices, enabling better integration within global supply chains and avoiding interoperability issues across national borders. Requirements should address a range of cybersecurity practices, such as adopting a risk-oriented approach (in accordance with Sections 4.6 on risk management and resilience and 5.3.2 on national risk assessment); protecting data and systems; securing procurement processes and supply chain; monitoring digital environments and detecting potential anomalies or events; and responding to and recovering from incidents, supported by well-defined incident and crisis management processes, business continuity measures, and disaster recovery plans.
Operators may also be required to maintain Security Operations Centers (SOCs) for real-time monitoring and incident response. Cybersecurity baselines should be proportionate to the risk profile and criticality of the operators involved. A tiered approach can be applied to differentiate between high-impact and lower-impact entities, ensuring efficient allocation of compliance efforts without undercutting core protections.
Cross-sectoral baselines should be developed first, enabling greater interoperability and consistency of sector-specific practices and streamlined compliance for cross-sector functions and subsectors. These can be complemented by sector-specific “how to” guidance, offering options to inform and integrate enterprise practices. These guidelines should also be supported by a set of oversight mechanisms (e.g., performance-based audits, self-assessments, mandatory reporting) to ensure that baseline requirements are not only adopted but also actively maintained.
Cybersecurity baselines should be outcome-focused to ensure greater agility over time as the risk landscape and technology continue to evolve. Articulating what operators should aim to achieve (e.g., “control logical access to critical resources”), rather than prescribing how they should implement security (e.g., “use two-factor authentication”), allows government and industry to benefit from continuous security improvements.
Framing requirements in outcome terms also enables flexibility in implementation, encourages innovation, and reduces the regulatory burden of constant updates. This approach is particularly valuable for adapting to emerging technologies and changing threat environments, as it avoids prematurely locking operators into specific technical solutions.
5.2.4 Employ a Combination of Policy Options
The Strategy should envisage the deployment of a wide range of policy tools to ensure that cybersecurity responsibilities are both enforceable and achievable, in accordance with the principle of a comprehensive approach and tailored priorities (Section 4.2).
To encourage operators across CI/CII/ES to adopt cybersecurity practices commensurate with the risks they face, governments should deploy a balanced mix of incentives and disincentives. Policy options may include: conducting audits and other compliance monitoring efforts; defining liability and accountability measures; developing certification and accreditation schemes; providing financial incentives and subsidies; delivering cyber capacity-building initiatives; and promoting structured public-private partnerships (PPP), such as sectoral Information Sharing and Analysis Centers (ISACs) or Information Sharing and Analysis Organizations (ISAOs), to facilitate cross-sector intelligence sharing and collective defense (Section 4.7 on using an appropriate set of policy instruments and Section 5.4.3 on promoting information-sharing).
Since operators may not fully internalize the broader societal impacts of cybersecurity incidents, policy interventions are often necessary to ensure that safeguards are adopted not only for corporate benefits but also for the broader public interest. Policy tools should therefore be carefully calibrated to address the gaps between what the markets can and should drive and what the evolving risk environment requires.
Where voluntary or market-based solutions prove insufficient, the Strategy should recognize the role of targeted regulation or direct public intervention, particularly in high-risk or low-competition sectors. At the same time, effective policy frameworks should avoid overregulation that could stifle innovation or duplicate existing efforts, instead streamlining requirements across public and private entities.
Finally, the Strategy should promote regular evaluation of these policy tools, using metrics to assess behavior change, resilience outcomes, and market responsiveness. Adjustments should be made over time based on emerging risks, new technological developments, and lessons learned from implementation. Embedding this review cycle reinforces accountability, ensures sustained alignment with national priorities, and supports long-term resilience across CI/CII/ES (Lifecycle Section).
5.3 Focus Area 3 – Risk Management in National Cybersecurity
This focus area introduces good practices for addressing cybersecurity through risk management. As stipulated in the principle of risk management and resilience (Section 4.6), a risk management approach should be adopted, since cybersecurity risks cannot be fully eliminated. Ensuring that a country has a clear understanding of the risks that it faces allows it to prioritize resources, reduce vulnerabilities, and improve overall preparedness. Moreover, the risk management approach should align with national priorities and consider the digital environment in its entirety, in accordance with the principle of comprehensive approach and tailored priorities (Section 4.2). It should focus on identifying interdependencies within and across sectors, as well as risks arising from cross-border dependencies.
The Strategy should ensure that risk management is not treated as a one-time exercise, but as a continuous, data-driven process that integrates strategic foresight, sectoral intelligence, and evolving threat landscapes. Given that cybersecurity threats and the digital environment are extremely dynamic and unpredictable, any risk management approach should be reviewed regularly and designed to address unknown risks. As such, the Strategy should plan for monitoring and evaluation of risk management activities to strengthen resilience and ensure continuous improvement. This includes establishing institutional responsibilities for oversight, evaluation, and refinement of risk management frameworks at national, sectoral, and organizational levels.
5.3.1 Assess National Cybersecurity Risk
The Strategy should promote regular identification, analysis, and assessment of cybersecurity risk at the national level, guided by a formal and repeatable approach. This typically entails estimating the likelihood and potential impact of cybersecurity incidents based on threats, vulnerabilities, and interdependencies of societal functions. Assessments should be dynamic, incorporating threat intelligence, cross-border and geopolitical considerations, and emerging technological risks such as those posed by advances in AI or quantum computing.
The assessment could include sectoral risk profiles for those sectors deemed most critical to society and the economy. Sectoral risk profiles provide a basis for more specific risk assessments and help introduce coherence within and across all sectors nationally. In addition, the assessment should consider CI/CII/ES (Section 5.2.2) and their interdependencies within and across sectors (e.g., between energy, telecommunications, water, and healthcare). It should identify systemic cybersecurity risks whose impacts may cascade across interconnected systems and disrupt the continuity of essential services.
The Strategy should define governance mechanisms for conducting and updating national and sectoral risk assessments, specifying the roles of national cybersecurity authorities, sectoral regulators, intelligence agencies, and key private stakeholders in contributing to and validating the assessment. Such efforts will inform and help align cyber risk management strategies with the country’s crisis management plan, while also mobilizing the necessary capabilities, capacities, expertise, funding, and policies to strengthen the overall national cybersecurity posture.
5.3.2 Develop a National Framework to Manage Cybersecurity Risk
The Strategy should promote the development and implementation of a national framework for the consistent and coordinated management of cybersecurity risk across interdependent sectors and assets. The framework should establish a national risk register, securely stored and communicated, to provide government visibility and oversight of risks and approaches taken to manage them. The framework should prioritize risks based on the probability of occurrence and their potential impact. The risk register should consider the nation’s risk appetite and tolerance levels across different sectors and functions and guide risk classification accordingly. The national risk register should be dynamic and updated at regular intervals (e.g., annually or after major incidents) based on evolving threats and technology.
The framework should also include mechanisms for aggregating sectoral and organizational risk data, while respecting confidentiality and data protection requirements, to ensure strategic-level visibility without exposing sensitive operational details. It should specify the responsibilities of key entities in each sector for the assessment, acceptance, and treatment of national-level cybersecurity risks, ensuring accountability and clear reporting lines, and supporting coordinated decision-making, such as escalation protocols and decision-making pathways, related to systemic cybersecurity risks.
Additionally, the Strategy should encourage the definition of national-level risk metrics to assess the effectiveness of cybersecurity measures, along with feedback mechanisms to support continuous policy improvement and inform future strategic and operational decisions.
5.3.3 Establish a Common Methodology for Managing Cybersecurity Risk
The Strategy should promote the establishment of a common methodology for managing cybersecurity risks. This will ensure efficiency and consistency across organizations and facilitate the exchange of threat and risk information across interdependent systems. A methodology based on international standards should be favored, as it may reduce costs and improve interaction with the private sector. This common methodology should be adaptable to sector-specific needs and flexible enough to incorporate future changes in technology and threat actors.
The methodology should provide guidance on the full risk management lifecycle, from assessing threats to valuing assets, defining risk appetite and tolerance levels, implementing and maintaining mitigating measures, and accepting residual risk. It should also include a certification program to assess and improve compliance. This certification should be scalable and tiered, offering different levels of controls for organizations of varying sizes and criticality, and aligned with national compliance frameworks as well as relevant international obligations.
Importantly, for the procurement of digital infrastructures or services, the risk management methodology should provide guidance on mechanisms for enhancing the reliability of the supply chain. It should also promote secure-by-design and secure-by-default principles.
5.3.4 Establish Cybersecurity Policies for Risk Management
The Strategy should encourage the establishment of national cybersecurity policies, adopted in accordance with the principle of an appropriate set of policy instruments (Section 4.7) and the principle of comprehensive approach and tailored priorities (Section 4.2). These policies should cover governance, operational, and technical requirements; clarify stakeholder roles and responsibilities; and mandate specific approaches to these issues. To ensure coherence, the Strategy should promote the development of a national cybersecurity policy framework that aligns sectoral efforts, eliminates redundancy, and defines minimum expectations across critical sectors.
Examples of such policies could include requirements for cybersecurity in secure procurement, information-sharing programs, coordinated vulnerability disclosure, minimum security baselines and standards of care, certification programs for compliance, and mandatory reporting to competent authorities. These policies should also define procedures for timely, secure, and standardized incident notification, ensuring compatibility with sector-specific and cross-border reporting obligations.
A coordinated national policy framework would lead to more efficient and effective cybersecurity management, as it would harmonize practices, reduce redundancy, and ensure consistency and interoperability across sectors. To this end, the Strategy should establish mechanisms for policy coordination among regulators, agencies, and private sector stakeholders, such as national working groups, interagency task forces, or advisory councils, with clearly defined mandates and reporting responsibilities to ensure that cybersecurity policies are consistently applied and remain fit for purpose.
5.4 Focus Area 4 – Incident Response
This focus area provides an overview of good practices that support the establishment and sustainability of national capabilities to prepare for, prevent, detect, mitigate, respond to, and recover from cybersecurity incidents, while improving a country’s overall cyber resilience.
5.4.1 Establish Cyber Incident Response Capabilities
The Strategy should call for the establishment of a national body that serves as a central point of contact to facilitate and coordinate national incident response capabilities across the country. Often, this involves the establishment of Computer Emergency Response Teams (CERTs), Computer Security Incident Response Teams (CSIRTs), or Computer Incident Response Teams (CIRTs)[1] with national responsibility.
The national CERT/CSIRT/CIRT may be complemented by sectoral or organizational teams (e.g., finance, health, energy, transport), which provide sector-specific services and act as intermediaries between organizations and the national CERT/CSIRT/CIRT.
The specific organizational model of a CERT/CSIRT/CIRT may vary (e.g., national, governmental, sectoral), and while not every country has the same needs and resources, these specialized and dedicated teams should provide both proactive and reactive functions, as well as preventive and educational services. These entities can increase a country’s ability to respond quickly and recover from incidents, while also reducing adverse impacts and strengthening resilience.
The core service areas that CERTs/CSIRTs/CIRTs typically offer include cyber incident response and coordination, vulnerability management, situational awareness (including threat intelligence and information sharing), and knowledge transfer. The national CERT/CSIRT/CIRT may also host the government Security Operation Center (SOC), providing services such as monitoring, detection, and management of information security events to public agencies.
The Strategy may also encourage the establishment of Security Operations Centers (SOCs) and Product Security Incident Response Teams (PSIRTs) by private-sector entities to enhance their ability to detect threats, manage events, and handle ICT product vulnerabilities. Ultimately, these entities serve as the first line of defense for the management and containment of incidents, feeding into the national response system.
The Strategy should also define and formalize cooperation mechanisms and communication procedures between national, sectoral, and private incident response teams, as well as with regional and/or international counterparts.
[1] While there are subtle distinctions in origin and usage, the terms CERT, CSIRT, and CIRT are widely used interchangeably within the incident response community. This guide references the CSIRT Services Framework developed by the Forum of Incident Response and Security Teams (FIRST) to describe the typical range of services offered by response teams https://www.first.org/standards/frameworks/csirts/csirt_services_framework_v2-1.
5.4.2 Establish Contingency Plans for Cybersecurity Crisis Management and Disaster Recovery
The Strategy should call for the development of a national contingency plan for cybersecurity emergencies and crises. The plan should be integrated into or aligned with the broader national contingency framework. Sector-specific plans for critical information infrastructures and essential services should also be considered.
This national cybersecurity contingency plan should integrate inputs from all stakeholders (Principle 4.3 on inclusiveness), as well as findings from national risk assessments and analysis of cross-sector dependencies that may affect the continuity of operations of CI/CII/ES. It should also define escalation procedures, incident categorization criteria, and disaster recovery mechanisms, ensuring clarity on how incidents are prioritized, communicated, and managed.
5.4.3 Promote Information Sharing
The Strategy should call for the establishment of information-sharing mechanisms to facilitate the exchange of actionable intelligence and threat information between and among the public and private sectors.
Formal and informal information-sharing programs can help improve coordination, foster timely and accurate communications during incident response and recovery, and enable the rapid dissemination of threat intelligence among affected parties and other stakeholders. These mechanisms help improve the understanding of how and which sectors have been targeted, identify measures that can be used to mitigate damage to affected assets, and ultimately reduce vulnerabilities and cascading impacts.
The Strategy should designate one or more institutional structures (e.g., CERT/CSIRT/CIRT) responsible for transmitting accurate and actionable information among national stakeholders, including both public and private actors. It may also encourage participation in structured information-sharing mechanisms, such as Information Sharing and Analysis Centers (ISACs), Information Sharing and Analysis Organizations (ISAOs), and other forms of Public-Private Partnerships (PPPs) and cooperative arrangements.
Importantly, information-sharing should be a two-way process. Government entities must contribute relevant information to demonstrate partnership and build trust, thereby encouraging private-sector entities to share their own insights in return. This reciprocal exchange ensures that incident responders remain focused on priority threats and are better prepared to respond effectively.
5.4.4 Conduct Cybersecurity Exercises
The Strategy should encourage the organization and coordination of domestic and international cybersecurity and incident response exercises at the strategic and operational levels. These exercises may take the form of simulations, tabletop exercises, or live operational drills, and should engage both technical and non-technical audiences.
Cybersecurity exercises and related crisis-planning mechanisms can help countries test response procedures, validate communication channels, develop required skills (see Section 5.5 on Capacity-Building), and evaluate the operational readiness of CERTs/CSIRTs/CIRTs to respond to cybersecurity incidents and service disruptions under pressure. They also enhance understanding of cross-sector dependencies and foster institutional capacity for incident response.
Similarly, regional and international cybersecurity exercises can strengthen cyber incident response capabilities across borders, improve understanding of interdependencies, build confidence and trust between governments, stimulate information sharing and collaboration for investigative and judicial cooperation, and enhance collective resilience and preparedness.
5.4.5 Establish Impact or Severity Assessment of Cybersecurity Incidents
The Strategy should encourage the establishment of standardized mechanisms to assess and categorize cybersecurity incidents based on their severity and impact. These assessments aim to evaluate the broader context of cyber-related incidents, including potential and actual impacts on critical sectors, infrastructures, services, and population groups, as well as cascading effects across interdependent systems.
Assessments should be conducted transparently and collaboratively, engaging a wide range of stakeholders. They should be integrated into national disaster recovery and contingency plans, with outcomes feeding directly into the national cyber incident response framework and informing future policy refinements.
5.5 Focus Area 5 – Capability and Capacity-Building, and Awareness Raising
Technology and policy frameworks often dominate cybersecurity discourse, yet it is the human element, skills, awareness, and institutional capacity, that ultimately determines the effectiveness of a country’s cyber resilience. This focus area addresses the challenges related to advancing cybersecurity capacity across all levels of society by advancing cyber safety, addressing behaviors, awareness, and cyber hygiene in the digital environment. It focuses on both human and institutional development, aiming to raise awareness among key stakeholders, including government entities, citizens, academia, and the private sector, which are crucial to enabling a country’s digital economy.
Good practices considered in this section include the strategic planning and coordination of capacity-building activities, workforce development programs, the integration of cybersecurity curricula into formal education, and the implementation of targeted awareness-raising campaigns. Furthermore, the section highlights how fostering research, innovation, and cross-sector collaboration between the government, private sector, and academia can enhance national capabilities and support long-term sustainability of cybersecurity efforts.
5.5.1 Strategically Plan Capacity Building and Awareness Raising
Strategic planning is the foundation of effective cyber capacity-building and awareness raising. This process should distinguish between long-term human capital development, which aims to strengthen national expertise and workforce pipelines over a Strategy’s lifecycle, and shorter-term capacity-building efforts, such as targeted training and public awareness campaigns. A well-articulated plan allows for coordination, resource optimization, and accountability across different actors and levels of government.
Long-term human capital planning requires a whole-of-governmental approach, convening relevant ministries, such as education, foreign affairs, justice, labor, economy, and digital affairs, alongside national cybersecurity authorities. This planning process should be evidence-based, identifying future cyber-skills needs, developing national cybersecurity workforce frameworks, and defining measurable KPIs linked to clear implementation pathways from early education through university, postgraduate programs, and advanced research. It should also include timelines, funding models, and mechanisms for periodic review and adjustment.
Importantly, planning the expansion of the cybersecurity workforce presents an opportunity to promote inclusion and gender equality by cultivating expertise across underrepresented communities, rural and economically disadvantaged populations, and women, thereby addressing national-level skills gaps through equitable access to capacity-development opportunities.
The planning process should also guide shorter-term capacity-building initiatives, including executive and operational training, drills, simulations, awareness-raising, and other public outreach activities, such as engagement in events linked to Cybersecurity Awareness Month. While less resource-intensive, these activities require strategic oversight to remain relevant, inclusive, and responsive to changing threat landscapes, communication channels, and public behaviors. These activities should be coordinated and overseen by the competent national cybersecurity agency and embedded throughout the Strategy’s implementation period.
A tripartite partnership among government, academia, and the private sector is essential to this planning process, balancing workforce supply and national cyber skills demand. In this collaboration, governments provide direction and incentives, academic institutions and training providers deliver education and skills, and the private sector contributes hands-on experience, innovation, and funding support. This partnership also plays a strategic role in cultivating innovation and entrepreneurship, strengthening the national ecosystem, and supporting the development of a sustainable, forward-looking cybersecurity workforce.
Finally, given national differences in priorities, maturity, and resource level, there is no one-size-fits-all approach to cyber capacity-building. The information gathered should therefore be used to design approaches tailored to each country’s specific political, economic, and social context.
5.5.2 Strengthen the Cybersecurity Education Pathway
The Strategy should facilitate the development or expansion of dedicated cybersecurity education pathways aimed at accelerating cybersecurity skills development and awareness throughout the entire formal education system, from early education to higher education and professional training. Curricula should be interdisciplinary and multidisciplinary, covering not only technical but also non-technical cybersecurity skills and topics such as digital literacy, public policy, law, governance, economics, risk management, ethics, social sciences, and international relations.
At the primary and secondary levels, the focus should be on building foundational digital literacy and promoting safe online behavior. In tertiary education, more specialized and advanced programs should be developed, including the integration of cybersecurity courses in all computer science and IT programs, as well as the creation of dedicated cybersecurity degrees and apprenticeships. Apprenticeship programs should be developed through collaborative efforts between government, industry, and educational institutions to ensure that the knowledge and skills acquired through formal education are directly applicable in practice and aligned with industry needs, creating a continuous learning loop that supports both workforce readiness and long-term career development. Adult learners and professionals may require flexible, short-term programs focused on reskilling or upskilling to address evolving workforce demands.
Given the multi-disciplinary nature of cybersecurity education, universities, colleges, training centers, and other educational institutions should be encouraged to work across departments and in partnership with academic and private sector stakeholders to optimize resources and efforts when developing or updating their programs. These institutions can play a critical role in educating the workforce on the unique tenets of cybersecurity and can serve as incubators for the future workforce by combining theory, methodology, tools, and implementation, and by leveraging campus-wide resources to merge knowledge with practical skills.
Strategies could also include the development of cybersecurity workforce frameworks. These frameworks provide a structured approach to identifying, developing, and aligning cybersecurity roles, competencies, and training opportunities across sectors. They support strategic workforce planning and help align educational initiatives with current and emerging industry needs. For example, existing SOCs and PSIRTs could be leveraged as practical training environments or internship opportunities for students wishing to enter operational and product-security roles.
Additionally, curricula should foster awareness of and stimulate interest in cybersecurity career opportunities. To further the efforts, the government and the private sector should consider establishing various incentive schemes, such as scholarships, grants, and private-public partnerships, to support learners and trainees at all levels, particularly in underrepresented communities.
5.5.3 Stimulate Capacity Development and Workforce Training
The Strategy should encourage the development of cybersecurity training and skills development schemes for experts and non-experts in both public and private sectors. This effort could include the provision of executive and operational training, formal internships, traineeships, mentorships, and national or international certifications for security professionals, based on needs identified by industry and government. The Strategy should also encourage targeted training for national-level actors involved in domestic and foreign policy, including regulators and legislators. Trainings should be complemented with initiatives focused on cyber risk management, and with practical exercises within and among government entities and other stakeholders, such as drills and simulations.
These initiatives should target a wide range of beneficiaries, including professionals seeking to enter or advance in the cybersecurity field, public officials, and non-experts whose work intersects with cybersecurity. Government, academia, the private sector, and civil society should act as key implementers and enablers, collaborating to design and deliver training that meets the evolving needs of the cybersecurity ecosystem.
The Strategy should also foster initiatives that aim to develop dedicated cybersecurity career paths and an effective pipeline of future employees, particularly for the public sector, and promote incentives to increase the supply of qualified cybersecurity professionals and help retain talent. These should be created in partnership with academia, the private sector, and civil society.
To address the ongoing gender gap in cybersecurity, a gender-balanced approach that motivates, encourages, and facilitates greater engagement from women should be considered across all efforts aimed at skills development and training. The Strategy should also promote inclusive approaches that reach other underrepresented groups, such as individuals from geographically remote or economically disadvantaged areas, minority communities, and those with disabilities and neurodivergent profiles, many of whom hold significant untapped potential. To attract and retain diverse talent, the Strategy should therefore address accessibility and inclusion at every stage of the talent pipeline.
5.5.4 Implement a Coordinated Cybersecurity Awareness-Raising Program
Entities responsible for cybersecurity awareness campaigns and activities at the national level should collaborate with relevant stakeholders to develop and implement coordinated, data-driven programs focusing on disseminating information about cybersecurity risks and threats, as well as best practices for countering them.
Such efforts could include partnerships with private sector actors, such as banks, telecommunications providers, and digital and social media platforms, that are often best positioned to deliver targeted awareness campaigns on specific cybersecurity risks relevant to their user base, such as financial scams, phishing, and data privacy threats.
5.5.5 Tailor Programs for Vulnerable Sectors and Groups
The Strategy should identify groups in society that require particular attention regarding cyber capacity-building and awareness-raising. Cybersecurity awareness programs could include a variety of initiatives tailored to different audiences: the general public, children, the elderly, individuals with disabilities, digitally challenged populations, schoolteachers, social workers, and executives across the public and private sectors. These programs should explicitly address issues such as cyberbullying, sexual harassment, and online safety. They should promote a culture of cyber hygiene, the responsible use of technology, and critical thinking skills to help individuals identify and respond to online risks.
Tailored programs should be developed for sectors identified as being particularly at risk or in need of empowerment to protect themselves, such as small- and medium-sized enterprises (SMEs), community-based organizations (CBOs), underserved communities or low-income communities.
5.5.6 Foster Cybersecurity Innovation and Research and Development (R&D)
The Strategy should foster an environment that stimulates basic and applied research in cybersecurity across sectors and stakeholder groups. Such initiatives include, for example, ensuring that national research efforts support the objectives of the Strategy, developing cybersecurity-focused R&D programs in public research organizations, effectively developing and disseminating new findings, baseline technologies, techniques, processes, and tools. The Strategy should also aim to develop an efficient, competitive, and sustainable local market for cybersecurity services.
In addition, the Strategy should also promote continuous research into evolving cyber risks affecting diverse population groups, such as youth, the elderly, small businesses, or rural communities, to inform the design of targeted training programs and awareness campaigns that are both relevant and effective.
To this end, governments should promote close collaboration with academia and the private sector to support a dynamic cybersecurity ecosystem. Targeted support for startups and SMEs, including access to funding and incubation programs, can help build a competitive domestic market and ensure the broad availability of cybersecurity products and services.
To promote the development of such solutions, the Strategy could explore incentive mechanisms, including grants, procurement programs, tax credits, competitions, and other initiatives that encourage the development of innovative cybersecurity solutions, products, and services.
Moreover, countries should seek to establish ties with the international research community in the scientific fields related to cybersecurity, such as computer science, electrical engineering, applied mathematics, and cryptography, as well as in non-technical fields such as social and political sciences, business and management studies, criminology, law, and psychology.
5.6 Focus Area 6 – Legislation and Regulation
This focus area covers legal and regulatory aspects that should be addressed as part of a national cybersecurity strategy. The Strategy should call for a legal framework to establish cybersecurity mandates and responsibilities, protect society against cybercrime and the misuse of technology, and foster a digital environment in line with the principles of inclusiveness, fundamental human rights, and a trust environment (Sections 4.3, 4.5, and 4.9, respectively). The legal framework should, at a minimum, align with the country’s obligations under international, regional, and national human rights law, and should include:
- Establishing or clarifying the roles and responsibilities of national cybersecurity authorities, sector-specific regulators, and coordination mechanisms.
- Granting legal authority to designate critical information infrastructure, together with risk management obligations, security controls, mandatory incident reporting requirements, and national incident reporting platforms.
- Defining substantive cybercrime offenses in criminal law and providing procedural powers and safeguards for investigation, prosecution, and international cooperation.
- Providing compliance, enforcement, and oversight mechanisms, including audit authority, corrective measures, sanctions, and review procedures.
- Enabling international cooperation through cross-border information sharing, mutual legal assistance, and participation in multilateral cybersecurity coordination frameworks.
- Embedding provisions for sustained legal capacity development, regulatory institutionalization, and adaptation of the framework over time in line with international developments.
The Strategy should map the relationship between policy objectives and the legal and regulatory framework, including operational aspects, and should identify gaps, and signal areas where legislative or regulatory adjustment may be needed. It should also recognize the breadth of the legal framework, covering primary legislation, secondary instruments, technical standards, industry codes of practice, and guidelines, and define a process for regular review to ensure proportionality, rights protection, technological responsiveness, and coherence with both domestic and international standards.
5.6.1 Establish a Domestic Legal Framework for Cybersecurity
The Strategy should promote the development of a domestic legal framework that grants clear statutory authority to assign institutional roles, define regulatory mandates, and coordinate the responsibilities of government agencies, sector regulators, and other relevant stakeholders.
The legal framework should set out clear competences to designate CI, CII, and ES, and impose cybersecurity obligations on operators. A statutory designation mechanism should ensure precision, predictability, and proportionality in assigning such obligations (e.g., a tiered obligation structure based on impact criteria; see Sections 5.2.2 and 5.2.3). Transparent designation criteria should guarantee consistent application of rules, while administrative and judicial review procedures should allow operators to appeal designations, dispute regulators’ decisions, or challenge sanctions through clearly defined legal channels.
A well-defined legal foundation ensures that limited regulatory resources prioritize entities whose compromise would have national-level impacts. It should also be adaptable to technological developments, in line with the principle of technological foresight and adaptability (Section 4.10), and clearly define the relationship between overarching cybersecurity law and sectoral regulatory regimes, ensuring coherence and avoiding both overlap and regulatory gaps.
5.6.2 Establish a Domestic Legal Framework on Cybercrime and Electronic Evidence
The Strategy should promote the development of a domestic legal framework that clearly defines cybercrime and related criminal offences, and provides adequate procedural powers for effective investigation, prosecution, and adjudication based on admissible electronic evidence.
The framework should define aspects such as substantive criminal offences, procedural powers for the collection of electronic evidence, and evidentiary rules addressing collection, authentication, integrity, chain of custody, and admissibility. Jurisdictional provisions should specify the application of national law to offences committed domestically, against domestic systems, by nationals abroad, or with extraterritorial effects, applying territorial, nationality, or effects-based principles as appropriate.
It should also establish the legal authority for international cooperation (Section 5.7.2), including mutual legal assistance, joint investigative teams, extradition, and participation in international cooperation mechanisms, and should seek alignment with international and regional instruments to ensure effective cross-border enforcement.
In addition, operational aspects of cybercrime investigation and prosecution may be addressed in secondary instruments, such as establishing specialized units, building digital forensic capabilities, developing standard operating procedures (SOPs), and setting up structured crime-reporting mechanisms.
5.6.3 Recognize and Safeguard Human Rights and Liberties
The Strategy should pay particular attention to technology-related legal issues that can affect the level of cybersecurity and have impacts on human rights (e.g., encryption, anonymity, responsible vulnerability disclosure, ethical hacking, and others). In doing so, the Strategy should ensure that both technical security measures and criminal justice responses are consistent with constitutional principles and applicable international human rights obligations (Section 4.5). Differences between cybersecurity (technical and preventive measures) and cybercrime (criminal justice responses) should be recognized and addressed in a manner that maintains the appropriate balance between security and rights protection.
One aspect that may be addressed in the legal framework design considerations as part of the NCS is the definition of how personal data may be processed for legitimate cybersecurity and cybercrime purposes, while embedding safeguards that uphold data protection principles. Data protection rules should be integrated into cybersecurity and law enforcement frameworks to ensure protection from unlawful access and use, and proper handling of personal data during investigations and incident response.
Safeguards for investigatory powers should require judicial or independent authorization, be grounded in the principles of necessity and proportionality, and provide effective legal remedies for individuals affected by state surveillance or investigative measures. Strategic considerations regarding cybercrime legislation should establish lawful tools for authorities to investigate and prosecute serious offences, while embedding procedural protections to prevent overbroad surveillance, politically motivated prosecutions, or violations of privacy rights. The Strategy’s legal considerations should also consider how to prevent the criminalization of legitimate cybersecurity activities, such as ethical hacking, penetration testing, coordinated vulnerability disclosure, or security research, which contribute to a safer digital environment.
5.6.4 Create Compliance Mechanisms
The Strategy should promote the establishment of compliance, enforcement, and oversight mechanisms to ensure that the legal framework for cybersecurity and cybercrime is effectively implemented and enforced. Legislation should convert statutory obligations into clear, auditable requirements, preserve legal certainty for regulated entities, maintain institutional accountability, and provide defined legal avenues to contest enforcement actions.
The framework should grant competent authorities supervisory powers to conduct audits, inspections, compliance monitoring, and reviews of incident response, as well as to issue corrective orders with remediation deadlines and impose proportionate administrative, financial, or operational sanctions. Oversight mandates should be clearly allocated among national cybersecurity authorities, sector-specific regulators, and coordination bodies to prevent duplication, fragmentation, or conflicting requirements.
Given the potential legal and economic consequences of enforcement decisions, procedural safeguards should ensure transparency, proportionality, and fairness. These include defined administrative appeal procedures, judicial review options, and legal standards for assessing the justification and reasonableness of sanctions.
Enforcement should be balanced with incentives that promote voluntary reporting and cross-sector information sharing. Safe harbor provisions for timely, good-faith incident disclosure, confidentiality protections for shared threat intelligence, and explicit separation between enforcement functions and cooperative information-sharing functions (e.g., CERTs/CIRTs/CSIRTs, SOCs, ISACs/ISAOs, or PSIRTs) can help maintain trust and encourage collaboration, while ensuring accountability.
5.6.5 Promote Legal Harmonization and Cross-Border Cooperation
The Strategy should recognize the cross-border dimension of cybersecurity, consider the ratification of international cooperation agreements, and encourage the alignment of the national legal framework with international cooperation standards. Shared standards support legal certainty and the protection of national interests and priorities in cross-border data sharing and cybersecurity efforts spanning multiple jurisdictions.
The legal framework should grant national authorities clear powers to engage in structured international cooperation while safeguarding domestic mandates and national security priorities. These provisions should enable timely information sharing and ensure consistent handling of shared data under confidentiality and data protection rules. They should also facilitate mutual legal assistance and cross-border investigations, support coordinated responses to cybersecurity incidents, and provide mechanisms for resolving jurisdictional conflicts.
Additionally, the Strategy should promote harmonization of national legislation with regional and international instruments, such as the Council of Europe Convention on Cybercrime (Budapest Convention), the UN Convention against Cybercrime (2024), OECD recommendations, Mutual Legal Assistance Treaties (MLATs), and other relevant frameworks. Such integration should follow careful institutional tailoring to ensure legal and operational coherence and to avoid fragmented legislation, overlapping obligations across regulations, or mandates that exceed the administrative or technical capacity of national institutions and regulated entities.
5.7 Focus Area 7 – International Cooperation
This focus area emphasizes the elements that the Strategy should cover regarding the external cybersecurity engagements of a country at the bilateral, regional, and international levels. At the bilateral level, this could involve establishing cyber cooperation agreements with key partner countries, for instance, on information sharing, incident response, or cyber capacity-building. Regionally, the country should consider active participation in relevant regional organizations and frameworks that address cybersecurity-related matters. At the international level, engagement with global organizations, particularly the United Nations, standardization bodies, and intergovernmental or multistakeholder platforms, is essential. These efforts could also include public-private partnerships. Cooperation with private sector actors (e.g., antivirus companies, SOCs, PSIRTs, ISACs/ISAOs, the threat intelligence community, social media providers, and global digital platforms) should be recognized as an essential component of international cooperation.
With digitalization impacting all areas of international relations, including human rights, economic and social development, trade negotiations, commercial relations, the development and use of emerging and disruptive technologies, supply chain security, and broader issues of stability, peace, and conflict resolution, cybersecurity has become an indispensable part of a country’s foreign policy. The Strategy should therefore recognize the borderless nature and international dimension of cybersecurity, highlighting the need to engage in international discussions and to cooperate with national, regional, and international stakeholders, as well as civil society, industry, non-governmental organizations, and academia.
In doing so, the Strategy should consider existing regional and international frameworks to prevent fragmentation, leverage good practices, and facilitate cross-border collaboration. Engagement with international public and private stakeholders is key to fostering constructive dialogue, developing trust and cooperation mechanisms, finding mutually acceptable solutions, and addressing common challenges, while building a global understanding of the importance of cybersecurity and resilience. Regional and international cooperation should be fostered in harmony with the political, social, cultural, and economic priorities of the country, in line with the principle of a comprehensive approach and tailored priorities (Section 4.2).
5.7.1 Recognize Cybersecurity as a Component of Foreign Policy and Align Domestic and International Efforts
The Strategy should clearly articulate the government’s priority areas and indicate long-term objectives for international cooperation, including which stakeholders (e.g., public, private, regional, global) should be engaged.
The Strategy should express a commitment to international cooperation on cybersecurity and recognize cybersecurity issues as an integral component of the country’s foreign policy across all relevant areas, including international peace and security, trade negotiations, cybercrime, and cyber capacity-building (CCB).
Moreover, the Strategy should ensure consistency between the country’s domestic and foreign policy agendas and align national cybersecurity approaches with its international efforts. This includes adopting policies and harmonizing the national legal framework to reflect the country’s obligations and commitments under international law. Such areas might include, for instance, support for international cybersecurity norms and confidence-building measures (CBMs); commitment to CCB; participation in the development of international cybersecurity standards; and joining existing regional and international processes.
This may also require harmonization among different governmental entities (a whole-of-government approach), including the Head of State and Cabinet, Ministry of Foreign Affairs, Ministry of Digitalization (or Digital Transformation), Ministry of Industry and Trade, Ministry of Justice, Ministry of Defense, national CERT/CSIRT/CIRT, and other institutions with national security, cyber, or digital responsibilities. This ensures that positions expressed by one domestic entity at a negotiating table in the international arena are properly coordinated and aligned across government.
5.7.2 Engage in International Discussions and Commit to Implementation
The Strategy should identify specific international fora and cooperation mechanisms that the country will join or cooperate with at the bilateral, regional, and international levels to effectively engage on cyber-related issues. It should reaffirm the country’s commitment to the application of international law to cyberspace, including the Charter of the United Nations and international humanitarian and human rights law, and may also outline a national position on how international law applies to this domain.
The Strategy should commit to joining and implementing existing regional and international instruments aimed at combating cybercrime and addressing other cyber threats, such as the Council of Europe Convention on Cybercrime (Budapest Convention), the UN Convention against Cybercrime, or relevant regional conventions (Section 5.6.5). The Strategy should also acknowledge that many international trade agreements include digital or cyber provisions (e.g., cross-border data flows, dual-use technologies).
Commitments may include the implementation of the UN framework for responsible state behavior in the use of ICTs, endorsed by the General Assembly, encompassing norms, CBMs, and CCB. The Strategy may also emphasize participation in other relevant regional and international processes, such as the UN Global Mechanism on ICTs in the context of international security. The Global Mechanism is a state-led, permanent mechanism with the aim of promoting an open, secure, stable, accessible, and peaceful ICT environment.
To ensure credibility, the Strategy should stress measurable objectives, allocate adequate resources (human and financial), define mandates for international engagement, and establish accountability mechanisms for evaluating results.
5.7.3 Promote Formal and Informal Cooperation in Cyberspace
The Strategy should emphasize both formal and informal international cooperation mechanisms across the public and private sectors that the country intends to engage in. Formal cooperation refers to structured, often legally binding arrangements such as treaties, conventions, and institutional partnerships that promote collaboration on policy, legislation, and law enforcement (e.g., INTERPOL, WIPO). Informal cooperation involves more flexible, trust-based networks that enable the voluntary exchange of information and expertise, without legally binding commitments, such as multistakeholder forums (e.g., GFCE, IGF); incident response and threat-sharing mechanisms (e.g., FIRST, ISACs, ISAOs, SOC-CSIRT networks, the Global Intergovernmental Points of Contact Directory on the Use of ICTs in the Context of International Security); and regional trust-building initiatives. Participation in these efforts facilitates improved coordination, timely exchange of information among relevant authorities, and collaborative responses to threats and vulnerabilities. The Strategy should also support strengthening legal frameworks to facilitate international cooperation (Section 5.6.5).
5.7.4 Foster Capacity-Building for International Cooperation
As the country undertakes international engagements related to cyberspace, it will need to develop or expand competencies and skills across all relevant government bodies, including expertise on cyber diplomacy, international law, data protection and privacy, trade, emerging and disruptive technologies, supply chain security, and other digital matters.
In order to effectively engage in international discussions and cooperation, the Strategy should encourage the development of dedicated cyber diplomacy capacity within government, for example, by establishing a specialized office, appointing cyber diplomats, or designating trained personnel as focal points within existing government portfolios or ministries. These officials should be equipped to engage in international fora, negotiate cyber-related issues, and coordinate cross-border cybersecurity cooperation.
Other capacity-building priorities may include strengthening the ability of the national CERT/CSIRT/CIRT to cooperate internationally; enhancing law enforcement and judicial cooperation; building skills to apply international law and norms in cyberspace; and participating in international cyber exercises. Governments should leverage existing international capacity-building programs (e.g., GLACY+, Global Forum on Cyber Expertise (GFCE), INTERPOL, etc.) to develop these competencies. For instance, law enforcement capacity-building efforts can help local and national law enforcement agencies enhance their skills, knowledge, and technical capabilities to leverage high-tech tools and systems for cross-border cybercrime prevention, detection, investigation, and prosecution. They can also allow law enforcement to keep abreast of cybercrime trends and the ever-evolving threat landscape to stay ahead of crime.
The Strategy should also encourage peer learning, knowledge, and skills transfer with international partners, and emphasize participation in international cybersecurity exercises and cross-border incident response drills as both capacity-building and trust-building measures.